HSM for Dummies
Payment Systems: The Starting Point for HSMs
ATMs these days are standalone, multi-service units. But it’s taken development
cycles over multiple decades to get to this point. Following the launch of this
equipment, the international cash machine network grew and financial institutes
placed increasing focus on the security of network mainframes processing the
data. During the first few years, the encryption routines were an inherent part of
a mainframe’s data-processing program. The upshot of this was that sensitive,
cryptographic, key data was stored directly in the memory area of a mainframe.
Because people had access to these areas, however, the security risk soon became
obvious, and financial institutes had to find a solution. Furthermore, the solution
had to be in the form of a device operated externally to the mainframe that
could run the security code and that also provided a secure storage location for
the cryptographic keys.
The functionality of the ’finance HSM’ was essentially on the simple
side, but relatively critical in its effect. Financial institutes used, and
still use, the devices to store cryptographic keys with which finance applications
can derive card PINs of account numbers. The wording of
the policy is: ’All PINs must be kept in encrypted form, and plainformat
PINs may never be made accessible to unauthorized third parties.’
So, it became clear relatively quickly that financial institutes had
to deploy HSMs.
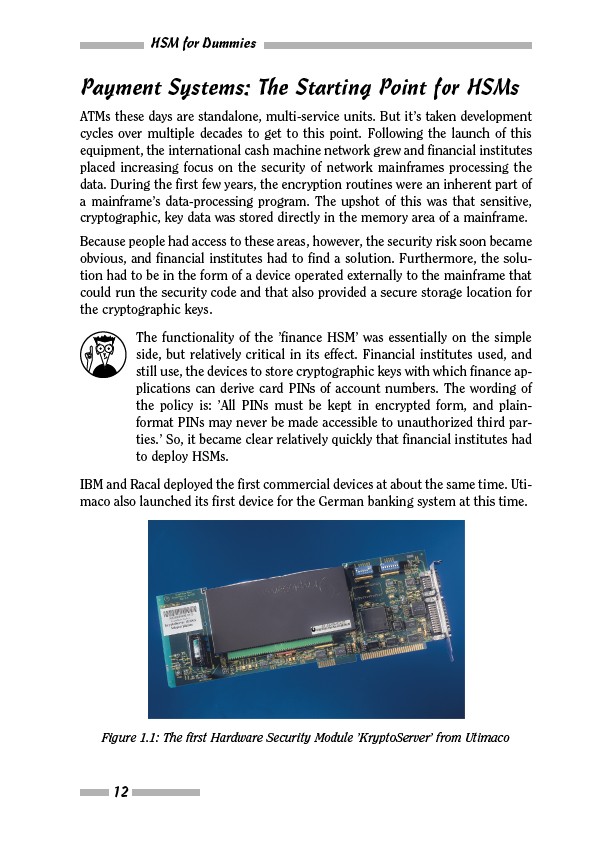
IBM and Racal deployed the first commercial devices at about the same time. Utimaco
also launched its first device for the German banking system at this time.
Figure 1.1: The first Hardware Security Module ’KryptoServer’ from Utimaco
12