HSM for Dummies
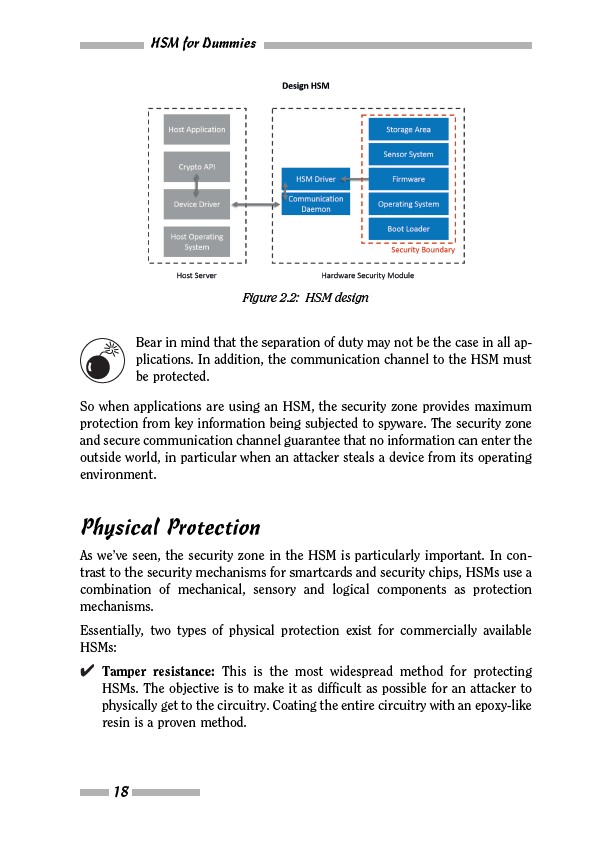
Figure 2.2: HSM design
Bear in mind that the separation of duty may not be the case in all applications.
In addition, the communication channel to the HSM must
be protected.
So when applications are using an HSM, the security zone provides maximum
protection from key information being subjected to spyware. The security zone
and secure communication channel guarantee that no information can enter the
outside world, in particular when an attacker steals a device from its operating
environment.
Physical Protection
As we’ve seen, the security zone in the HSM is particularly important. In contrast
to the security mechanisms for smartcards and security chips, HSMs use a
combination of mechanical, sensory and logical components as protection
mechanisms.
Essentially, two types of physical protection exist for commercially available
HSMs:
Tamper resistance: This is the most widespread method for protecting
HSMs. The objective is to make it as difficult as possible for an attacker to
physically get to the circuitry. Coating the entire circuitry with an epoxy-like
resin is a proven method.
18